External SSO based MFA
In order to enable the External MFA authentication:
Your instance must have external OIDC/SSO configured.
Select the VPN Location from the dropdown list on the Network Overview, and pressing the Edit Location button in the top right corner of the page.
Select the External MFA in the menu.
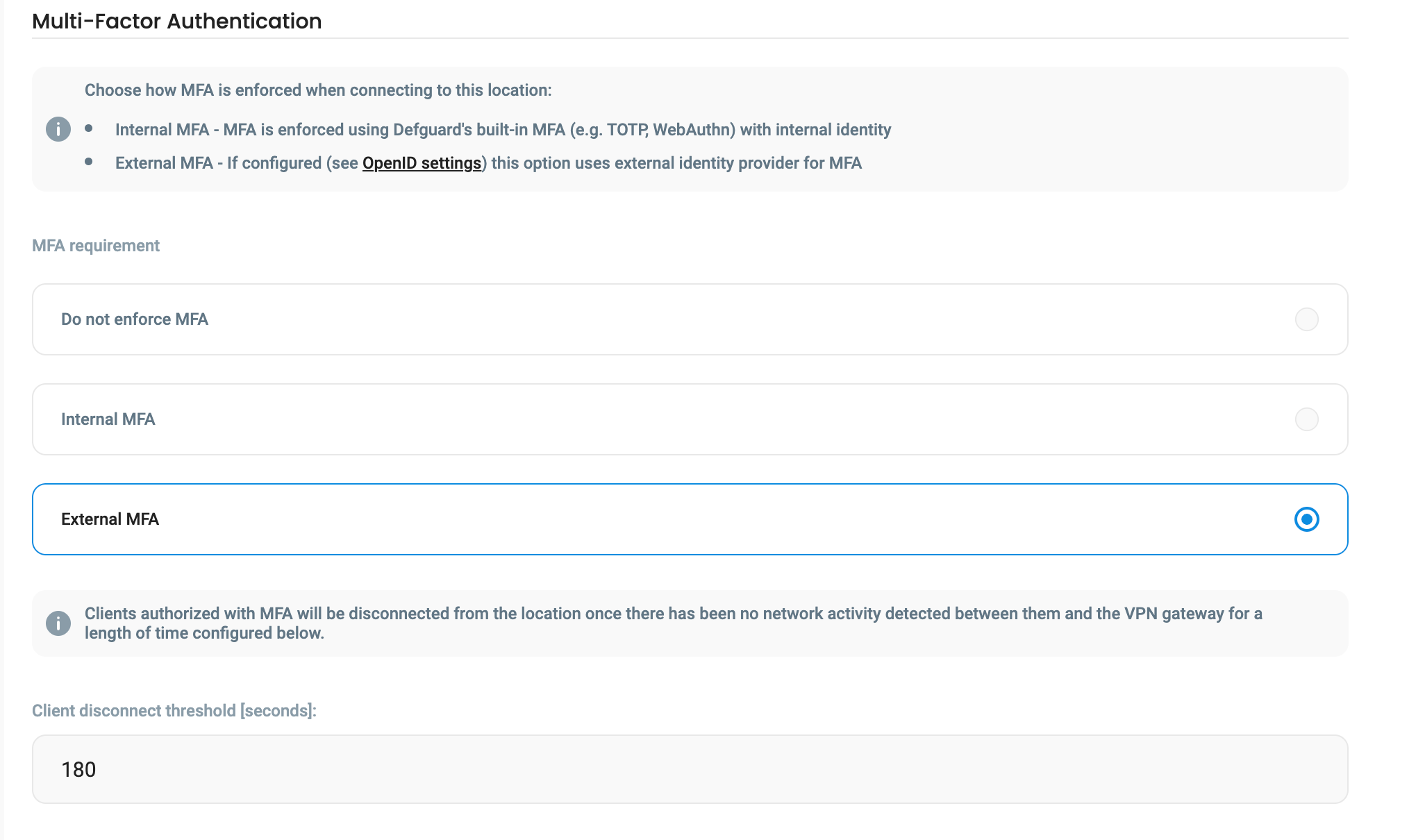
Client disconnect threshold
When MFA is enabled on a location, Defguard periodically (currently every 1 minute) checks statistics if a client is connected and if the period of inactivity (defined in this option) is met, a client is disconnected.
Thus, the gateway needs to be configured to send statistics in that period.
We recommend to set:
Gateway to send statistics every 30sec
Peer disconnect threshold we recommend it to be min. 300 (5 min)
Testing MFA on Defguard client
When a location has External MFA enabled, after clicking Connect in the Desktop client (here you can find information about Mobile Client External MFA), there will be information displayed about authentication requirement:
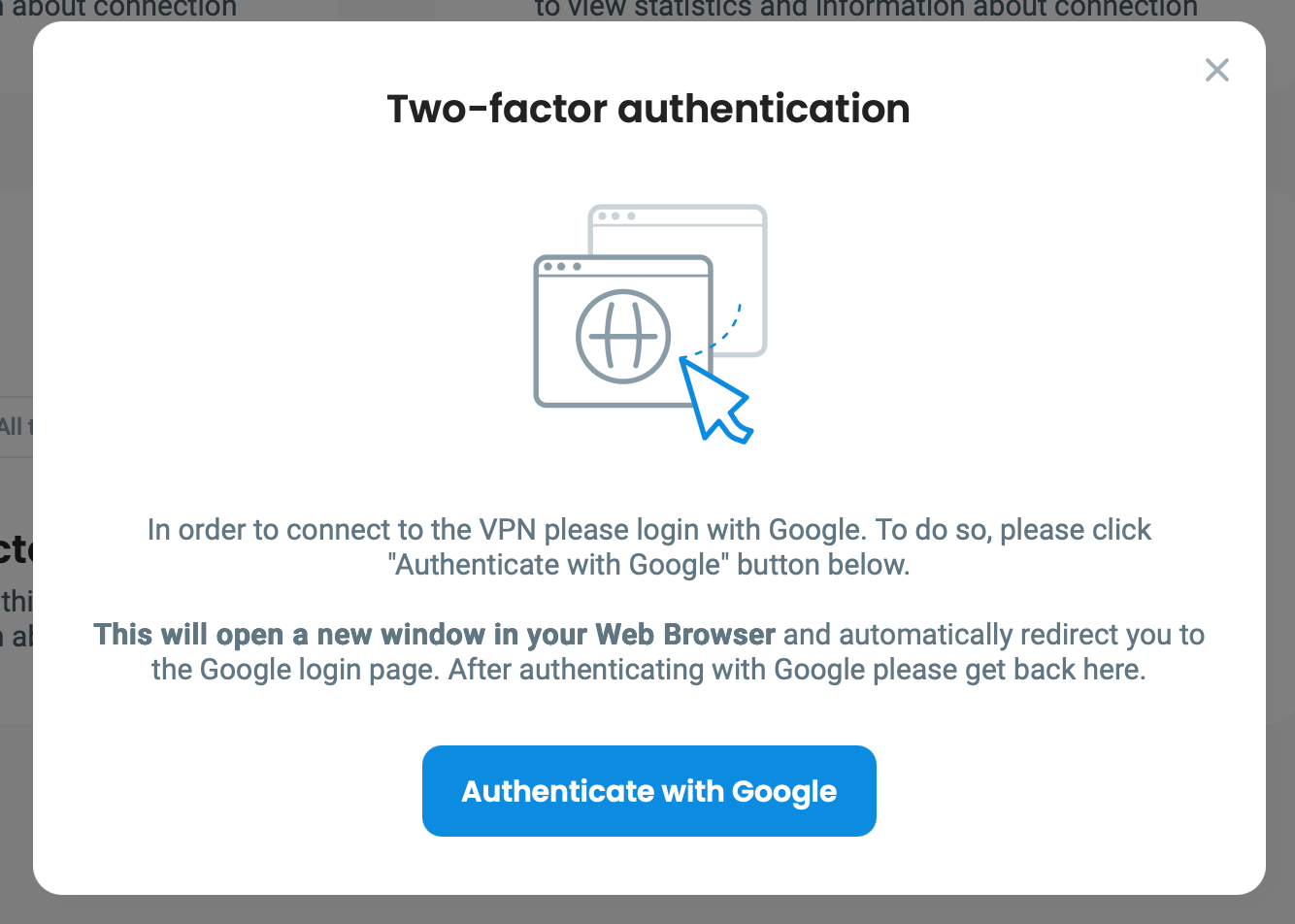
In order to authenticate the user will be prompted to click on Authenticate with your configured OIDC (like Authenticate with Google) - which will open the browser and start the authentication session with your OIDC/SSO provider by the Defguard Enrollment service (which is the only public component).
After successful authentication, the user will be informed by the enrollment service like so:
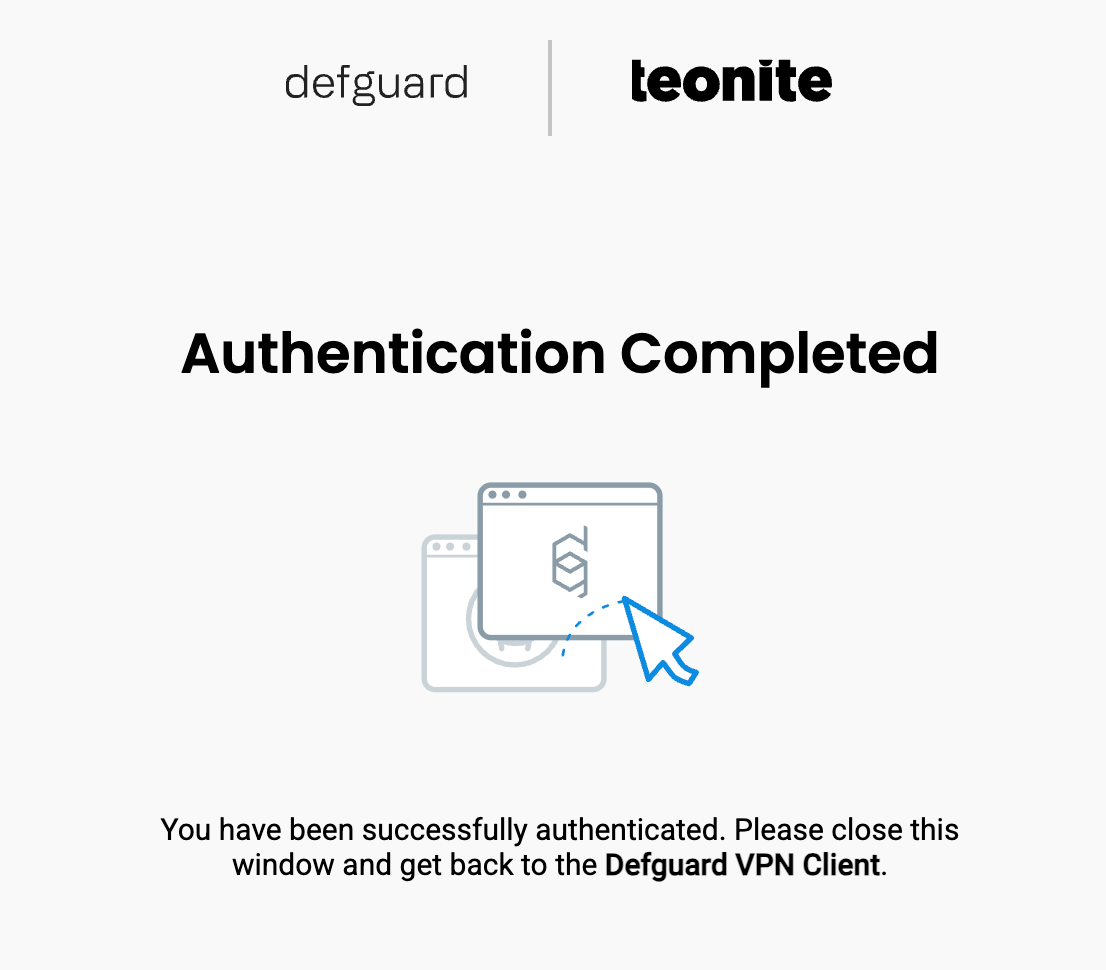
And the VPN should be connected.
Video describing whole process:
Biometry as an internal MFA method
Users can use biometry as an internal MFA method on their mobile devices. If a device has configured biometry as an MFA method, you will see ![]() icon, next to the device name.
icon, next to the device name.
Last updated
Was this helpful?